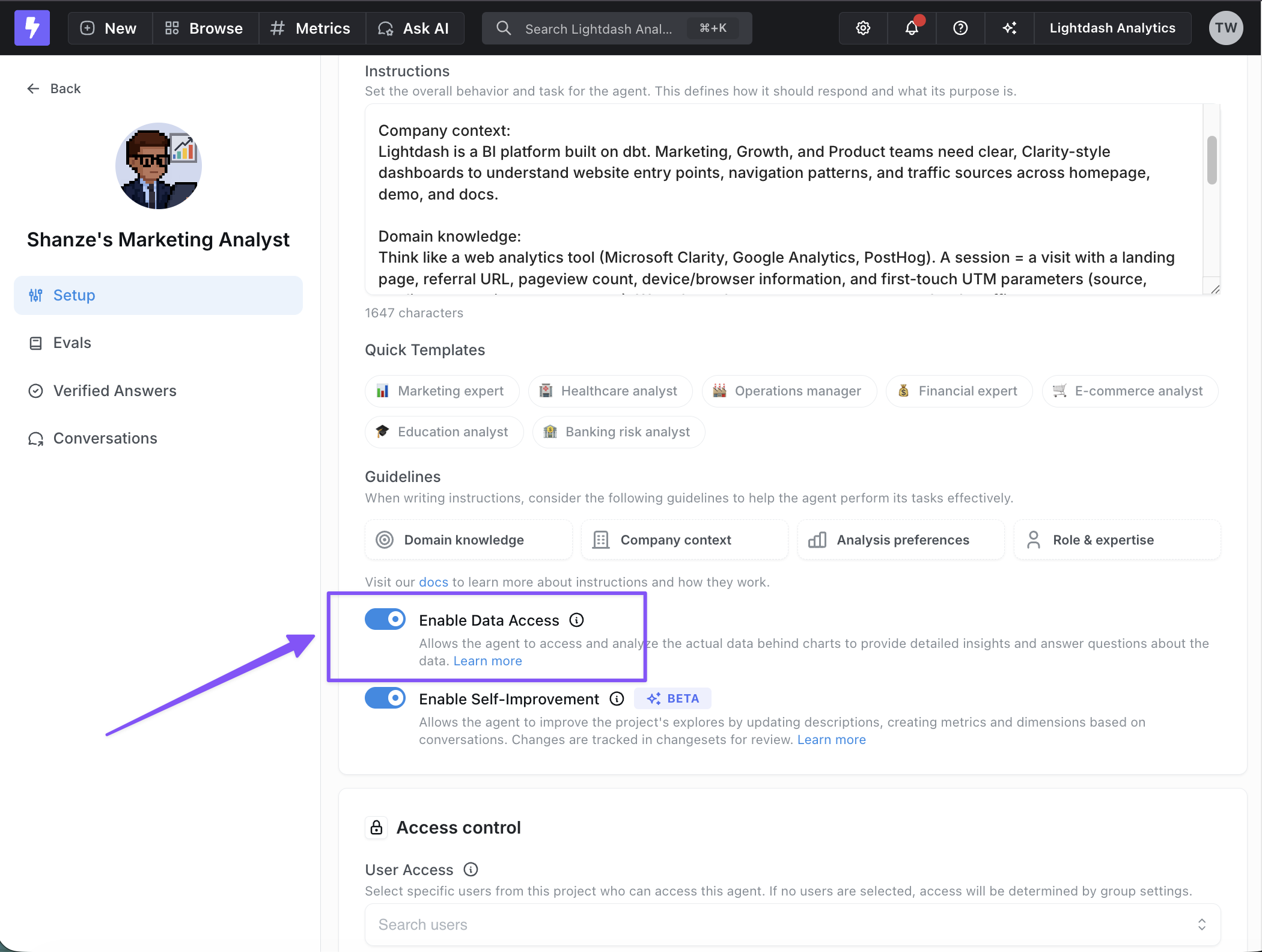
Data access modes
Metadata-only mode (default):- Agents can see your data structure, field names, and model definitions
- They can generate appropriate queries and visualizations
- No actual data values (except for one-row query results) are shared with the agent
- Perfect for exploring data structure and creating initial analyses
- Agents receive actual query results in addition to metadata
- Can provide specific insights, identify trends, and analyze patterns in your data
- Offers detailed summaries and data-driven recommendations
- Can search for actual field values to ensure accurate filters when building visualizations
- Only shares data when explicitly enabled per agent
Data access is optional and controlled per agent. When disabled, agents only
work with your data model structure and cannot see actual data values. This
ensures sensitive information is only shared when you explicitly choose to
enable this capability.
Limiting access to specific explores and fields
You can control which explores and fields your AI agent can access using tags. When you configure tags in your agent settings, the agent will only see explores and fields that have matching tags. Two tagging options:- Lightdash metadata tags - Tags defined in the Lightdash
metasection, which can be applied at both the table level (model) and column level (individual metrics and dimensions) - dbt tags - Native dbt tags applied at the table level
- Add one or more tags to your agent settings
- Fields or explores with any of those tags will be accessible to the agent
- If no tags are configured, the agent can access everything
- As you add tags, you can interactively explore which explores and fields will be available in the agent settings interface
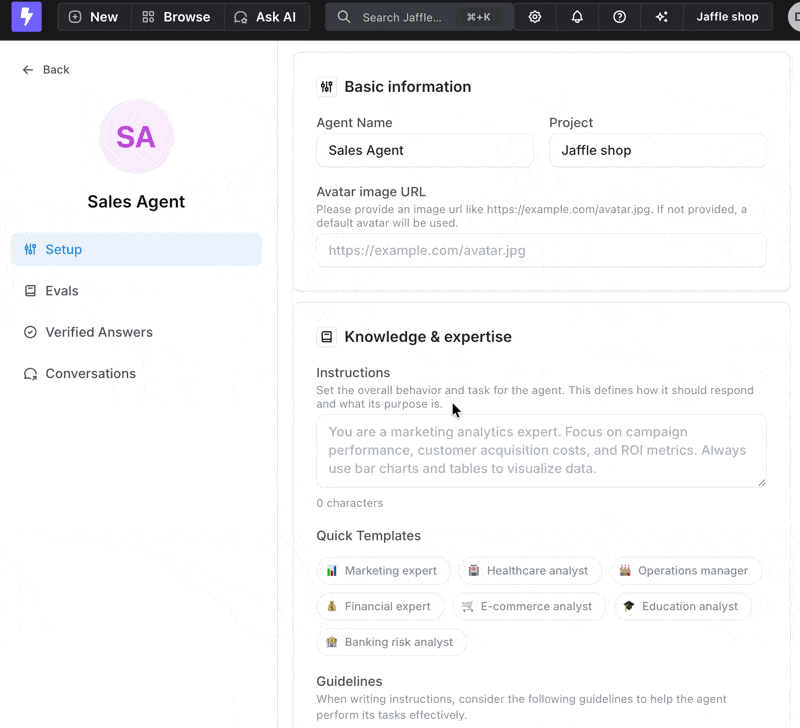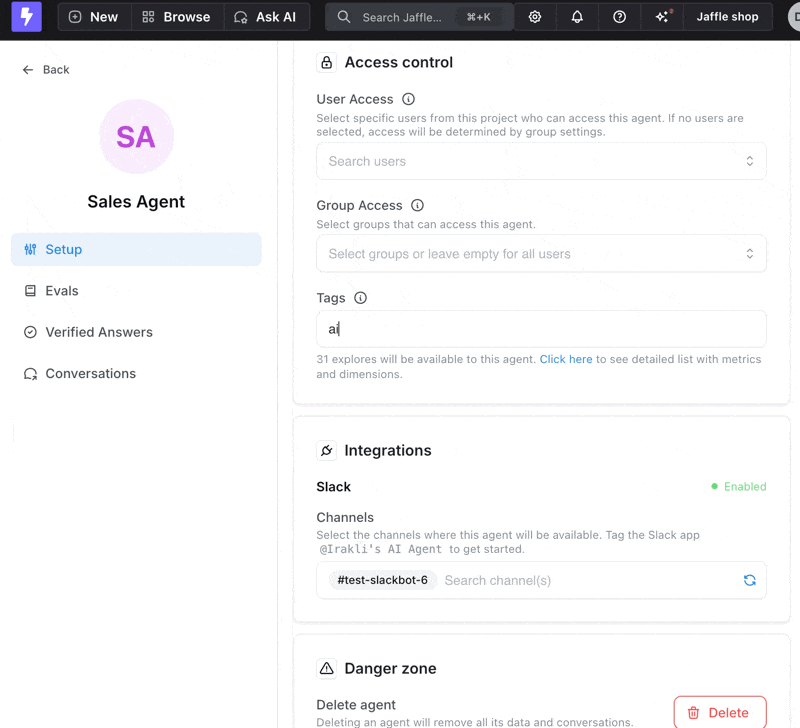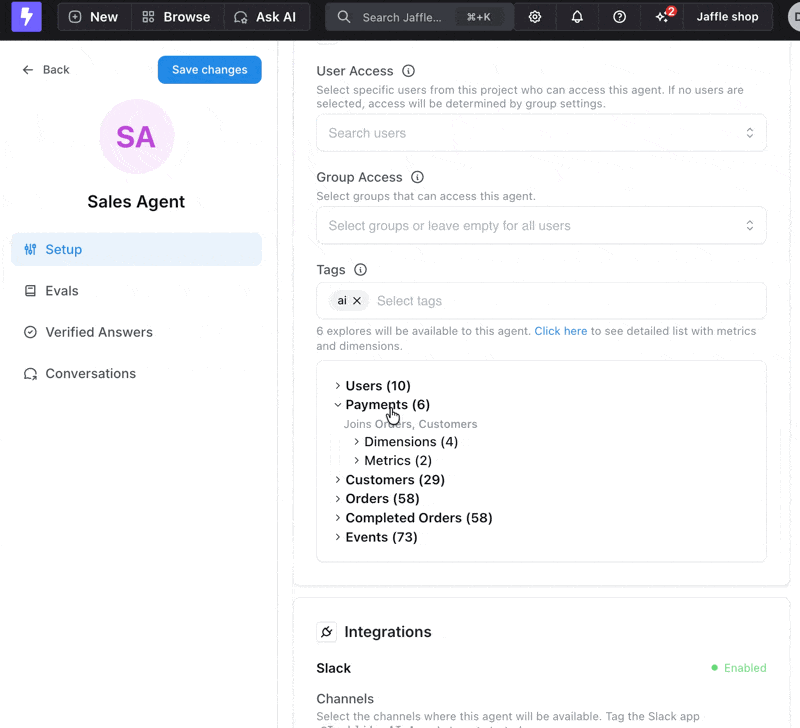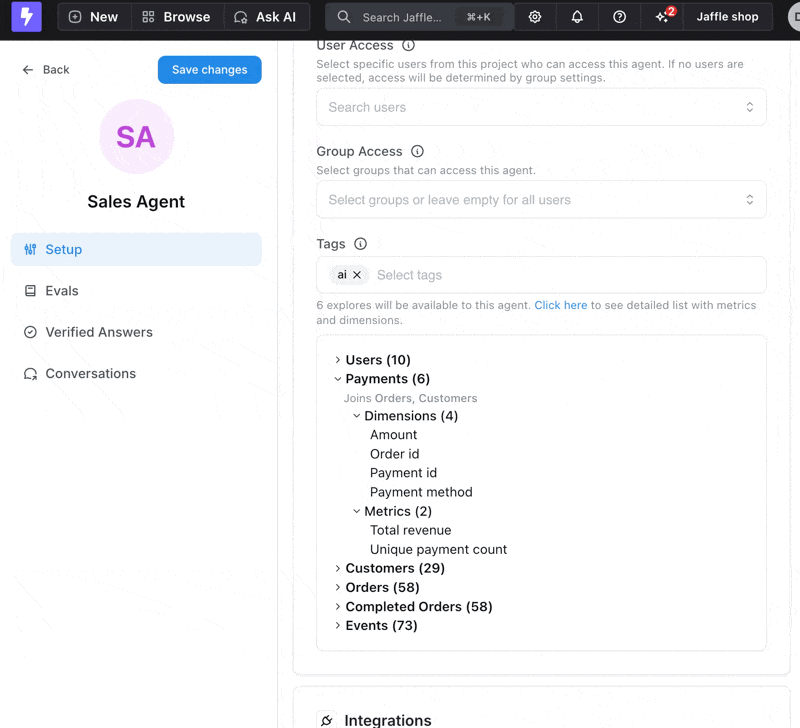
Preview available explores and fields as you add tags
- Explore-level tags - Tag the model to control access to entire explores
- Field-level tags - Tag individual metrics and dimensions for granular control
How filtering works
The filtering behavior depends on how you’ve tagged your models: Explore visibility:- An explore is only visible if its base table has matching tags at either:
- Explore level (model tags match agent tags), OR
- Field level (at least one base table field has matching tags)
- If only joined tables have matching tags but the base table doesn’t, the explore will be hidden
-
Field-level mode (when ANY field in the table has tags defined):
- Only fields with matching tags are visible
- Other fields are hidden, even if the explore is tagged
- Note: An empty tags array (
tags: []) activates field-level mode but matches nothing
-
Explore-level mode (when NO fields in the table have tags):
- If explore tags match: ALL fields in the table are visible
- If explore tags don’t match: NO fields are visible
Adding tags at the model level
Tag entire models to give your AI agent access to all metrics and dimensions within that explore:View code examples
View code examples
Adding tags to individual metrics & dimensions
For more granular control, tag specific metrics and dimensions:View code examples
View code examples
Common scenarios
Here are some common tagging scenarios and their results: Scenario 1: Explore-level only (no field tags)["ai-enabled"] tag, ALL fields in the customers explore are visible.
Scenario 2: Field-level only (no explore tags)
["ai-enabled"] tag, only customer_name is visible. The email field is hidden.
Scenario 3: Mixed - explore tagged with fields that have different tags
["ai-enabled"] tag, NO fields are visible. Field-level mode is active (because fields have tags), and none of the field tags match “ai-enabled”.
Scenario 4: Mixed mode - base model with explore tags, joined model with field tags
- orders.yml (base model)
- customers.yml (joined model)
["ai-enabled"] tag:
orderstable: ALL fields visible (explore-level mode - no field tags defined)customerstable: Onlyemailvisible (field-level mode - has field tags, onlyemailmatches)
- orders.yml (base model)
- customers.yml (joined model)
orders) has no matching tags.
User attributes and permissions
AI agents automatically respect all data access controls configured through user attributes. This ensures that agents only access data that the user is authorized to see, maintaining your existing security policies.How user attributes flow through AI queries
When an AI agent generates and executes queries on behalf of a user, it inherits that user’s attribute values and applies them to all data access: Row-level security:- Agents automatically apply
sql_filterrules defined in your models - Only rows matching the user’s attribute values are included in query results
- Example: If a user has
sales_region: 'EMEA', the agent will only query data for that region
- Agents respect
required_attributeson dimensions - Columns the user cannot access are invisible to the agent
- Metrics derived from restricted columns are also unavailable
- Example: If
salaryrequiresis_admin: 'true', non-admin users’ agents cannot query salary data
- Agents respect
required_attributeson models - Tables the user cannot access are completely hidden from the agent
- The agent cannot reference or join restricted tables
- Example: If
paymentsrequiresis_admin: 'true', non-admin users’ agents cannot query the payments table
Default behavior
In the Lightdash app: AI agents automatically use the logged-in user’s attributes for all queries.In Slack: AI agents currently use the attributes of the user who created the agent. We plan to respect user attributes based on Slack user email in the future—reach out if you need this feature!
How this works behind the scenes
When an agent generates a query:- The agent receives the user’s complete attribute profile (both direct user attributes and group attributes)
- All
sql_filterrules are automatically applied to the generated SQL - Dimensions and tables with
required_attributesare filtered from the available schema - The agent only sees and can query data within the user’s permissions
Example: Regional sales access
Consider this model configuration:sales_region: 'EMEA' and no can_view_pii attribute:
- The agent can query
revenuedata, but only for EMEA region - The agent cannot see or query
customer_name(PII restriction) - If the agent tries to analyze customer names, it will fail with a permissions error
- All generated queries automatically include
WHERE region IN ('EMEA')
Security considerations
- Metadata mode: Even in metadata-only mode, agents respect user attributes when showing available fields
- Data access mode: When data access is enabled, query results are filtered by user attributes
- Query generation: Agents cannot generate queries that bypass user attribute restrictions
- Error handling: If an agent attempts to access restricted data, the query fails with a permissions error